Windows Server RDL 远程执行漏洞风险提示和临时缓解工具
时间 : 2024年08月10日
1.漏洞概述
微软7月修复了3个Windows Server远程桌面授权服务(RDL)远程代码执行漏洞,漏洞编号分别是CVE-2024-38077、CVE-2024-38074和CVE-2024-38076。其中,CVE-2024-38077影响面最大,影响到17个Windows Server版本,CVE-2024-38074影响了13个Windows Server版本,CVE-2024-38076影响了7个Windows Server版本。Windows Server是微软公司推出的一款服务器操作系统,专为服务器环境设计,提供了丰富的功能和强大的网络管理能力,适合用于企业建站、网络应用、数据库管理等多个方面。
此次发现的漏洞只影响Windows Server版本,不影响其他Windows版本,该漏洞是存在于Windows远程桌面授权服务(RDL)中,由于该服务被广泛部署且开启Windows远程桌面(TCP:3389端口)的服务器,用于管理远程桌面连接许可,虽然该服务默认是不开启的,但因远程管理需求,管理员手动开启依然广泛。该漏洞是由Windows远程桌面授权服务中的堆缓冲区溢出引起的,可导致攻击者在未经身份验证的情况下远程执行任意代码。通过该漏洞,攻击者只须针对开启了相关服务的服务器发送特制数据包,即可完全控制目标系统,获得最高的SYSTEM权限。
2.漏洞影响范围
本次微软修复的3个Windows Server远程桌面授权服务(RDL)远程代码执行漏洞影响到的Windows Server版本如下所示。
|
漏洞编号 |
影响版本 |
|
CVE-2024-38077 |
Windows Server
2012 R2 (Server Core installation) |
|
Windows Server
2012 R2 |
|
|
Windows Server
2012 (Server Core installation) |
|
|
Windows Server
2012 |
|
|
Windows Server
2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) |
|
|
Windows Server
2008 R2 for x64-based Systems Service Pack 1 |
|
|
Windows Server
2008 for x64-based Systems Service Pack 2 (Server Core installation) |
|
|
Windows Server
2008 for x64-based Systems Service Pack 2 |
|
|
Windows Server
2008 for 32-bit Systems Service Pack 2 (Server Core installation) |
|
|
Windows Server
2008 for 32-bit Systems Service Pack 2 |
|
|
Windows Server
2016 (Server Core installation) |
|
|
Windows Server
2016 |
|
|
Windows Server
2022, 23H2 Edition (Server Core installation) |
|
|
Windows Server
2022 (Server Core installation) |
|
|
Windows Server
2022 |
|
|
Windows Server
2019 (Server Core installation) |
|
|
Windows Server
2019 |
|
|
CVE-2024-38074 |
Windows Server
2012 R2 (Server Core installation) |
|
Windows Server
2012 R2 |
|
|
Windows Server
2012 (Server Core installation) |
|
|
Windows Server
2012 |
|
|
Windows Server
2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) |
|
|
Windows Server
2008 R2 for x64-based Systems Service Pack 1 |
|
|
Windows Server
2016 (Server Core installation) |
|
|
Windows Server
2016 |
|
|
Windows Server
2022, 23H2 Edition (Server Core installation) |
|
|
Windows Server
2022 (Server Core installation) |
|
|
Windows Server
2022 |
|
|
Windows Server
2019 (Server Core installation) |
|
|
Windows Server
2019 |
|
|
CVE-2024-38076 |
Windows Server
2016 (Server Core installation) |
|
Windows Server
2016 |
|
|
Windows Server
2022, 23H2 Edition (Server Core installation) |
|
|
Windows Server
2022 (Server Core installation) |
|
|
Windows Server
2022 |
|
|
Windows Server
2019 (Server Core installation) |
|
|
Windows Server
2019 |
3.漏洞响应方案
3.1 漏洞官方修复方案
目前微软官方已发布安全补丁修复此漏洞,建议受影响的用户及时升级防护。
CVE-2024-38077漏洞补丁下载地址:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38077
|
产品 |
文章 |
下载 |
Build Number |
|
Windows Server
2008 for 32-bit Systems Service Pack 2 |
6.0.6003.22769 |
||
|
Windows Server
2008 for 32-bit Systems Service Pack 2 |
6.0.6003.22769 |
||
|
Windows Server
2008 for 32-bit Systems Service Pack 2 (Server Core installation) |
6.0.6003.22769 |
||
|
Windows Server
2008 for 32-bit Systems Service Pack 2 (Server Core installation) |
6.0.6003.22769 |
||
|
Windows Server
2008 for x64-based Systems Service Pack 2 |
6.0.6003.22769 |
||
|
Windows Server
2008 for x64-based Systems Service Pack 2 |
6.0.6003.22769 |
||
|
Windows Server
2008 for x64-based Systems Service Pack 2 (Server Core installation) |
6.0.6003.22769 |
||
|
Windows Server
2008 for x64-based Systems Service Pack 2 (Server Core installation) |
6.0.6003.22769 |
||
|
Windows Server
2008 R2 for x64-based Systems Service Pack 1 |
6.1.7601.27219 |
||
|
Windows Server
2008 R2 for x64-based Systems Service Pack 1 |
6.1.7601.27219 |
||
|
Windows Server
2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) |
6.1.7601.27219 |
||
|
Windows Server
2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) |
6.1.7601.27219 |
||
|
Windows Server
2012 |
6.2.9200.24975 |
||
|
Windows Server
2012 (Server Core installation) |
6.2.9200.24975 |
||
|
Windows Server
2012 R2 |
6.3.9600.22074 |
||
|
Windows Server
2012 R2 (Server Core installation) |
6.3.9600.22074 |
||
|
Windows Server
2016 |
10.0.14393.7159 |
||
|
Windows Server
2016 (Server Core installation) |
10.0.14393.7159 |
||
|
Windows Server
2019 |
10.0.17763.6054 |
||
|
Windows Server
2019 (Server Core installation) |
10.0.17763.6054 |
||
|
Windows Server
2022 |
10.0.20348.2582 |
||
|
Windows Server
2022 (Server Core installation) |
10.0.20348.2582 |
||
|
Windows Server
2022, 23H2 Edition (Server Core installation) |
10.0.25398.1009 |
CVE-2024-38074漏洞补丁下载地址:
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2024-38074
|
产品 |
文章 |
下载 |
Build Number |
|
Windows Server
2012 R2 (Server Core installation) |
6.3.9600.22074 |
||
|
Windows Server
2012 R2 |
6.3.9600.22074 |
||
|
Windows Server
2012 (Server Core installation) |
6.2.9200.24975 |
||
|
Windows Server
2012 |
6.2.9200.24975 |
||
|
Windows Server
2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) |
6.1.7601.27219 6.1.7601.27219 |
||
|
Windows Server
2008 R2 for x64-based Systems Service Pack 1 |
6.1.7601.27219 6.1.7601.27219 |
||
|
Windows Server
2016 (Server Core installation) |
10.0.14393.7159 |
||
|
Windows Server
2016 |
10.0.14393.7159 |
||
|
Windows Server
2022, 23H2 Edition (Server Core installation) |
10.0.25398.1009 |
||
|
Windows Server
2022 (Server Core installation) |
10.0.20348.2582 |
||
|
Windows Server
2022 |
10.0.20348.2582 |
||
|
Windows Server
2019 (Server Core installation) |
10.0.17763.6054 |
||
|
Windows Server
2019 |
10.0.17763.6054 |
CVE-2024-38076漏洞补丁下载地址:
|
产品 |
文章 |
下载 |
Build Number |
|
Windows Server
2016 (Server Core installation) |
10.0.14393.7159 |
||
|
Windows Server
2016 |
10.0.14393.7159 |
||
|
Windows Server
2022, 23H2 Edition (Server Core installation) |
10.0.25398.1009 |
||
|
Windows Server
2022 (Server Core installation) |
10.0.20348.2582 |
||
|
Windows Server
2022 |
10.0.20348.2582 |
||
|
Windows Server
2019 (Server Core installation) |
10.0.17763.6054 |
||
|
Windows Server
2019 |
10.0.17763.6054 |
3.2 漏洞临时缓解方案
目前微软官方给出的漏洞缓解方案是:在无需使用远程桌面许可服务(Remote Desktop Licensing)的Windows Server服务器上禁用此服务。注意:此操作将影响远程桌面的授权认证,可能导致远程桌面登录出现问题,影响正常业务。
需要注意的是,漏洞缓解方案并不能修复此漏洞!即便您关闭了此服务,我们也建议在适当时候安装从微软官方获得的补丁程序,彻底修复该漏洞!
3.3 使用安天漏洞应急工具缓急漏洞
安天CVE-2024-38077 漏洞应急处置工具是专项针对该漏洞的检测与处置工具,您可以通过本工具检查您的计算机是否会受到此次漏洞影响,并进行应急处置和补丁下载,此工具已上传至安天垂直响应平台(https://vs2.antiy.cn/)。
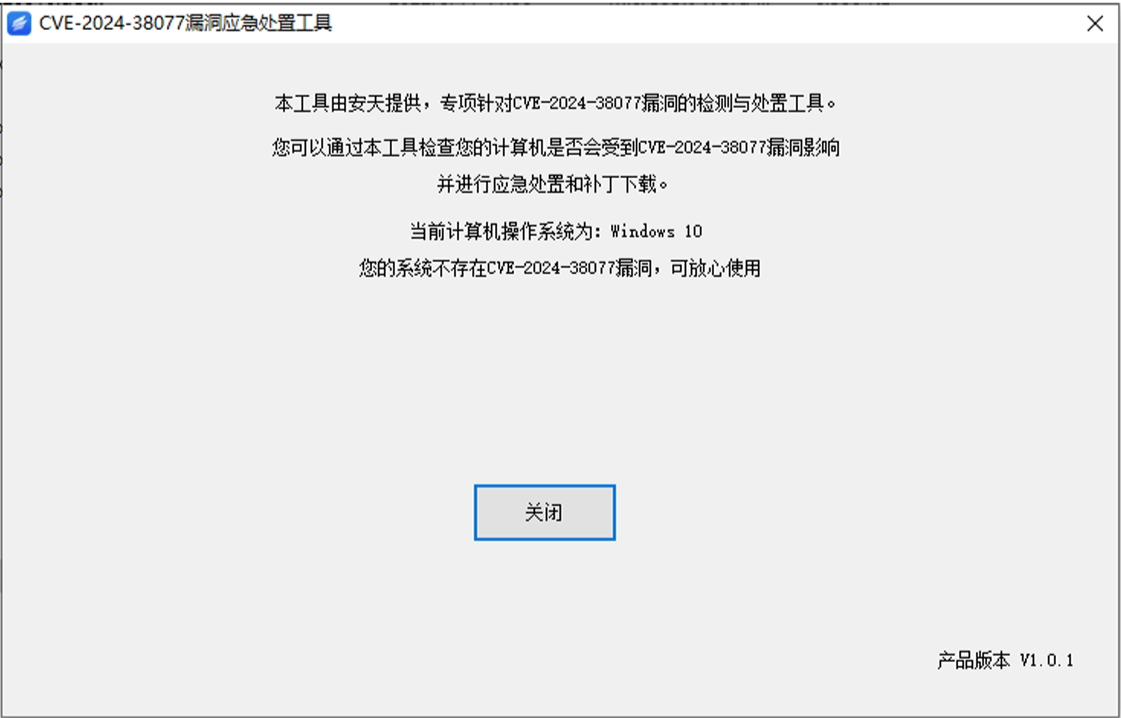
1. 启动程序与检测 双击“ATFixRDLTool.exe”启动程序,程序启动后将自动进行漏洞检测,如果当前计算机 操作系统版本不受该漏洞影响或者已修复该漏洞,则无需使用本工具进行处置。如果当前计算机操作系统版本存在该漏洞,工具将进行提示,您可以使用工具进行处置。
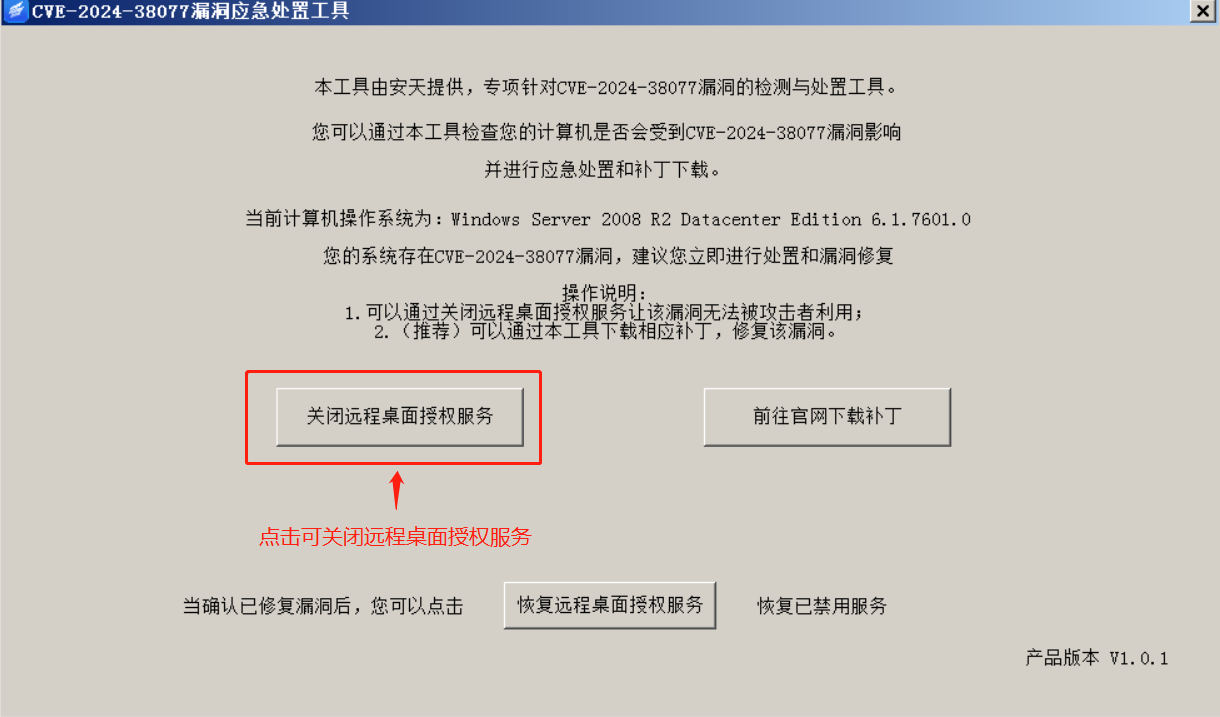
2. 漏洞处置 本工具提供了两种针对该漏洞的处置方式,其中:
a) 方法1:关闭远程桌面授权服务,关闭后攻击者将无法利用该漏洞进行攻击,但关闭该服务 在使用远程桌面服务时,最多将仅允许2个会话同时登录,并且该方法属于缓解措施,为确保 安全建议您尽快修复该漏洞。
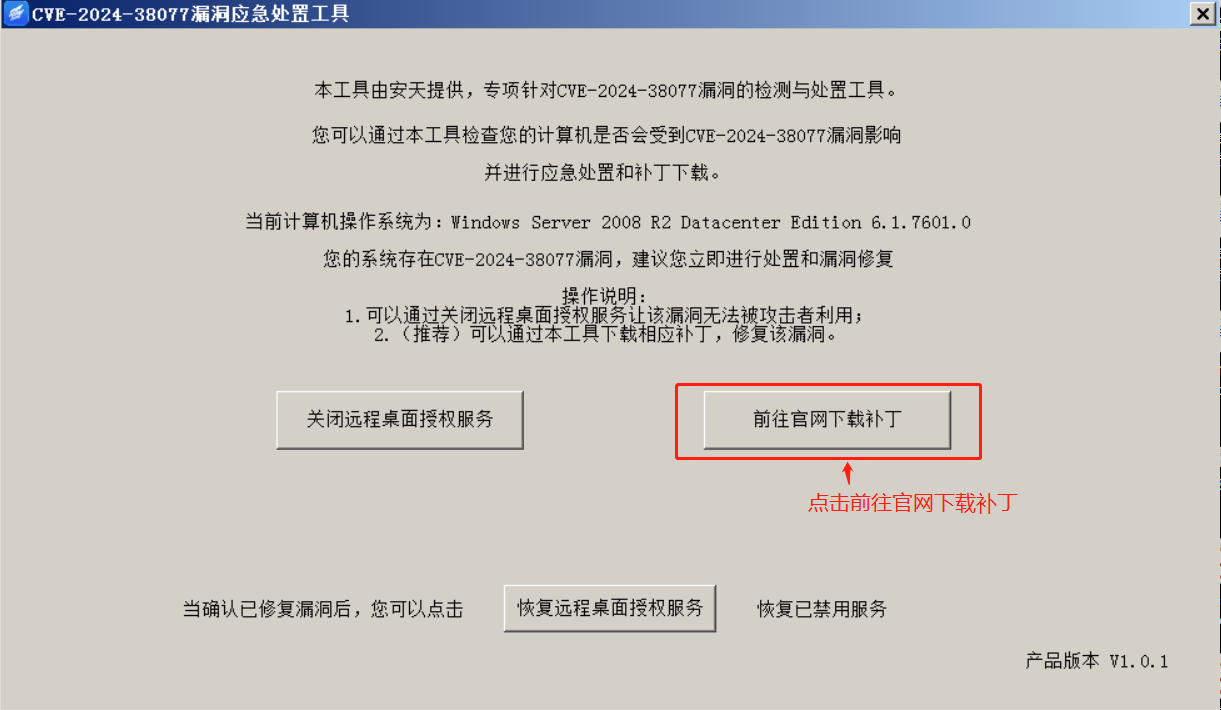
b) 方法2:点击“前往官网下载补丁”,工具将为您自动跳转至官方补丁下载页面,下载所需 补丁后在计算机本地运行安装即可,修复漏洞可以从根本上解决该问题,建议及时进行修复。注意,下载补丁需要计算机访问互联网
4.安全声明
本安全公告仅用来描述可能存在的安全问题,安天不为此安全公告提供任何保证或承诺。使用此安全公告应遵守相关法律法规规定。由于传播、利用此安全公告所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,安天以及安全公告作者不为此承担任何责任。
安天拥有对此安全公告的修改和解释权。如欲转载或传播此安全公告,必须保证此安全公告的完整性,包括版权声明等全部内容。未经安天允许,不得任意修改或者增减此安全公告内容,不得以任何方式将其用于商业目的。